Update: Sophos released an official guide on how to get Lync Web Services to work over the UTM’s WAF. https://sophserv.sophos.com/repo_kb/120454/file/Configuring%20UTM%20firewall%20for%20Lync%20connectivity.pdf
Using a Sophos UTM or Astaro Security Gateway (ASG) appliance? You can use it to reverse proxy to your Lync front ends!
v8 a feature called Web Application Firewall, which is a nicely wrapped version of Apache mod_proxy, and can be configured to reverse proxy your Lync Mobility and simple URLs, Office Web Apps and can also work with Exchange and pass Outlook Anywhere. The added benefit is that you can configure rules to block Cross-Site Scripting (XSS) and SQL Injection type attacks, among other things.
If you have the subscription, here’s how you set it up with Lync 2013:
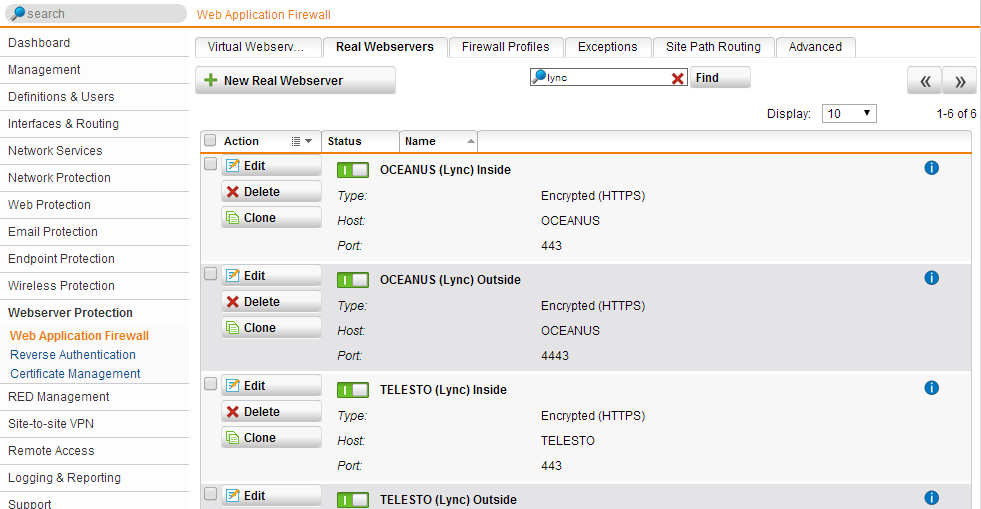
Configure your Lync Front Ends as Real Webservers. You will need to configure two servers for each FE, one for 8080 and another for 4443. If you plan on using the proxy for internal loopback (to avoid cert conflicts), then you will need 4 real servers, one for each port (80, 443, 4443, 8080). If you only want SSL, then skip the 80 and 8080:
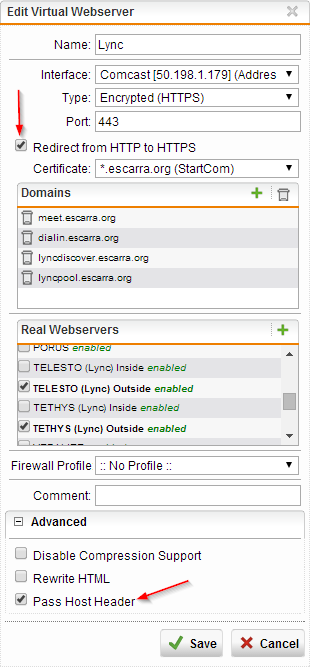
Then configure your Virtual Web Server (I will assume you already uploaded a valid certificate to the Sophos appliance). Make sure to check Pass Host Header, and you can enable HTTP redirection so your end users are happy when they skip HTTPS prefixes.
Save it, enable it, and DONE!
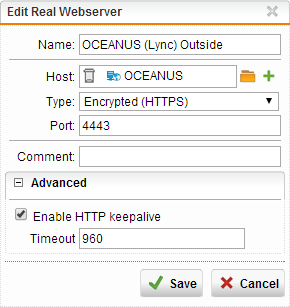
NOTE: If you have issues with the Lync iOS client resetting the connection, you can increase the timeout on the Real Webservers to 960 or 1200, but you will need to be on firmware version 9.204-19 or greater, since the feature was introduced then.