Both Lync and Exchange rely heavily on public-key encryption using X.509 certificates (commonly known as SSL Certificates), and so they are required in every implementation. Regardless of whether you are using a public certification authority like DigiCert, or host your own internal CA, generating, installing and managing certificates can get pretty complex, especially when you have to deal with Intermediate Certificates.
Certificate Chains can be a confusing concept and hopefully I do a good job in trying to explain them with a real-world analogy. Here goes:
Let’s say you are John Doe, a fellow citizen that obeys the laws and respects the rules and guidelines put forth by society, and you’ve been asked to make a State of the Union speech on national television. Sounds crazy, I know, but I had a hard time coming up with a better situation… (comments?)
Here’s one issue to tackle as soon as you show up on that big screen: “Who’s THIS guy?”. You begin your speech, and in the first few statements you say that you’ve been granted authority to speak by Senator Joe Smith, and that any questions of authority should be directed to him. Officially, the Senator endorsed (or signed for) you, John Doe the citizen.
Now, most people may not know Senator Joe Smith, but they do know the President of the United States. If you were to call the Senator and ask him for his authority or credentials, he will say he has been granted permission to act on the President’s behalf for the purpose of assigning someone to speak at the State of the Union speech. In other words, the President endorsed (or signed for) the Senator, who in turn signed for you.
If we were to break this down, John Doe citizen is the holder of the end LEAF certificate, the Senator is the INTERMEDIATE authority, and the President is the ROOT Certification Authority… Makes sense so far?
You were never technically granted authority to speak directly by the President. In fact, you were never in contact with him, and were only granted authority by an intermediary that has been endorsed by him. In this case, the CHAIN is:
Root (President) >Intermediary (Senator) > You (Citizen).
If during the initial stages of your speech you were to have said the President gave you authority, and everyone went to check with him, they would find that statement to be false. The President never directly endorsed YOU, therefore the chain is broken and cannot be validated. There’s something missing, and that’s the information about the intermediary. If you never send that chain information, some (or most) will not trust you, even if you claim to be authentic.
What does that mean in IT terms? Make sure your certificate chain is followed, and organize your certificates properly in your Certificates MMC on each system that presents them. Follow these rules:
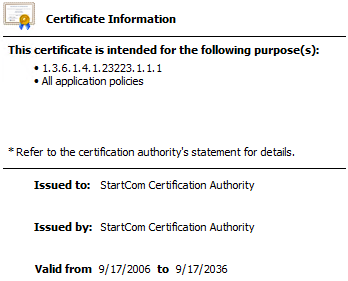
- Root CA certificates will always be self-signed and must be placed on the Trusted Root Certification Authorities store.
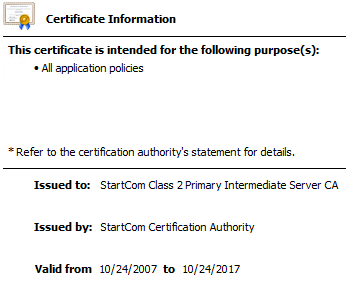
- Intermediate CA certificates will be signed by a Root CA or another Intermediate CA, and must be placed on the Intermediate Certification Authorities store.
- Your own certificates will be signed by either a Root CA (less likely) or an Intermediate CA (more likely), and should be stored in the Personal store.
Here are samples screenshots of the public certs I am using for my Lync lab:
Root CA (notice how it’s self-signed):
Intermediate CA (signed by the above Root CA):
Chain:
Hope this article didn’t get too messy or confusing. If you have any questions, please drop me a comment!