X.509 certs are annoying. You need to get them issued with the right names, or reissued if you make a mistake or forget a SAN, and they need to be cared for from time to time otherwise they expire and make your world hell.
Wouldn’t it be great if you could make them last longer than the default of 2 years? Especially if you’ve installed them all over your Lync infrastructure, like:
- Front End servers
- Mediation servers
- Edge server’s Inside NIC
- Office Web App Server
- Reverse Proxy or HLB
- Voice Gateways
- Exchange UM
Having to track and schedule downtime for cert renewal of all of the above components is quite the chore. So let’s extend it to 5 years using Microsoft Windows AD Certificate Services (AD CS)
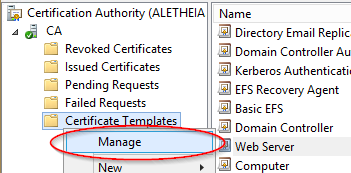
To start, we’ll duplicate the Web Server template. Open your Certification Authority MMC, go on your CA, and right click on Certificate Templates, then click Manage.
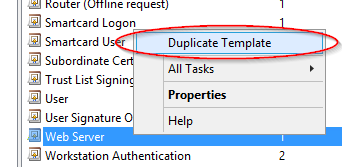
Right click on Web Server, then go on Duplicate Template.
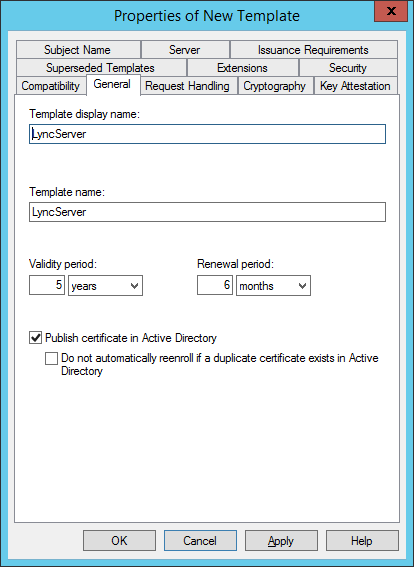
Under General, we will need to give it a name and Validity Period. I’ve chosen LyncServer but it can be anything. You will need the Template Name when getting certificates issued without auto-enrollment, like from an edge server, or from your voice gateway using a CSR.
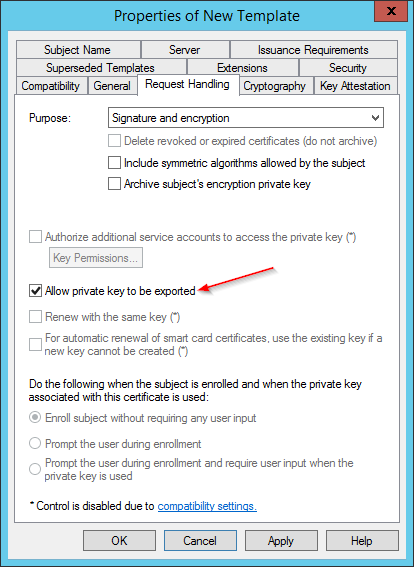
Under Request Handling, make sure to check Allow private key to be exported, review the other tabs and options to satisfy your curiosity, then click OK.
You can close the Certificate Templates Console and wait a bit for AD to replicate, or force it.
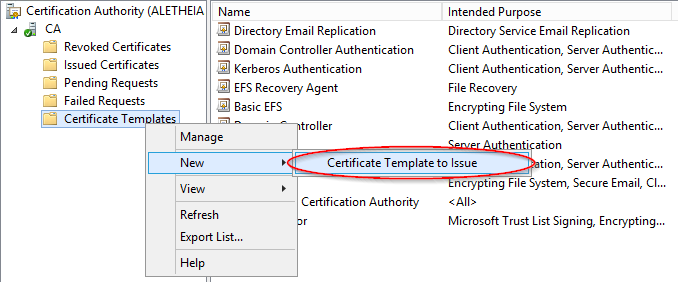
We will now enable the certificate so it can be issued. Right click on Certificate Templates again, then go on New, and Certificate Template to Issue. Look for your new LyncServer template, then click OK.
ONE LAST STEP!
On the CA server, you will need to extend the limit on the validity period, otherwise it will remain at 2 years regardless of what our template says. To do this, run:
certutil -setreg ca\ValidityPeriodUnits 5
certutil -setreg ca\ValidityPeriod years
The restart the Active Directory Certificate Services service, and the CA is now ready to start issuing longer certs!
When requesting certificates from Lync (or others), make sure to specify the template name when prompted. And if using a CSR for your gateway or edge servers, you can force the template attribute which is not included in the CSR, and is required by Windows to issue you a cert. To do that run:
certreq -attrib “CertificateTemplate:LyncServer”
Then pick the CSR, and then save the resulting signed certificate. BOOM!