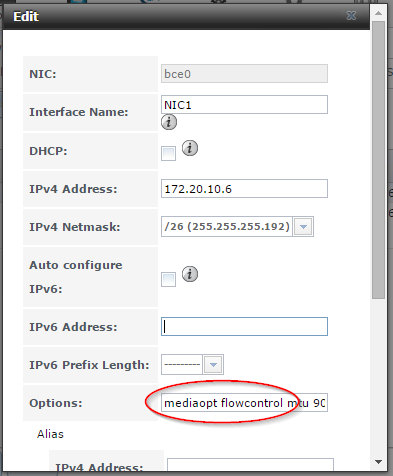
My switch kept complaining about the links to my FreeNAS SAN not supporting Flow Control. To enable it, edit the interface options in FreeNAS and ass mediaopt flowcontrol then save. Flow Control (and Jumbo Frames) is pretty important for iSCSI workloads to avoid dropped frames and uneven traffic.
Uncategorized
Music on Hold issue with AudioCodes and VVX
After a few hours of headscratching and a support ticket with AudioCodes I’ve resolved an issue that VVX phones have with Music on Hold through an AudioCodes gateway. All VVX phones are running UC firmware 5.2.0.8330, and someone else out there is having the exact same issue, but turns out the suggested fix of using voIpProt.SIP.useSendonlyHold=”0″ does not actually work in the 5.2 firmware.
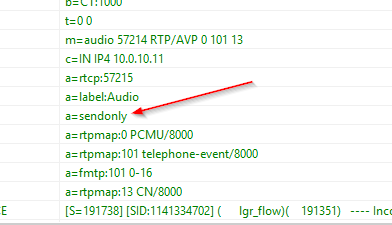
For a bit of background, what’s happening is the VVX sends a=sendonly in the SDP when a call gets put on hold, but Lync clients send a=inactive. The AudioCodes will play MOH when a=inactive is in the SDP, but not with sendonly, and there is only one behavior that can be configured.
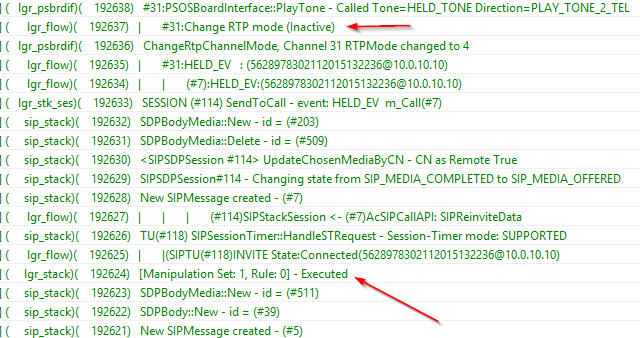
Setting the SendonlyHold flag in the config files did not make a difference, and the VVX’s were still sending the undesired SDP parameter, so the fix was to use a message manipulation rule on the AudioCodes to change it.
Going to VoIP > SIP Definitions > Msg Policy & Manipulation > Message Manipulations then creating the following is the first step:
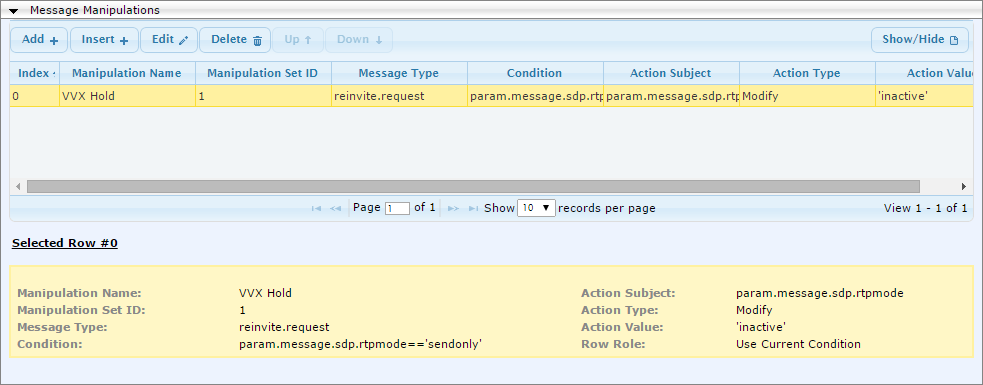
- Manipulation Name: VVX Hold
- Manipulation Set ID: 1
- Message Type: reinvite.request
- Condition: param.message.sdp.rtpmode==’sendonly’
- Action Subject: param.message.sdp.rtpmode
- Action Type: Modify
- Action Value: ‘inactive’
Then if you’re using SBC, you’ll need to apply the Manipulation Rule to the IP Group and call it a day… But in my case I’m using GW as the setup is from Lync to a PRI, and I could not associate the rule to the IP group for Lync. This was the difficult part because nothing I did applied that manipulation rule to Lync… then Janiel from AudioCodes came to the rescue with instructions:
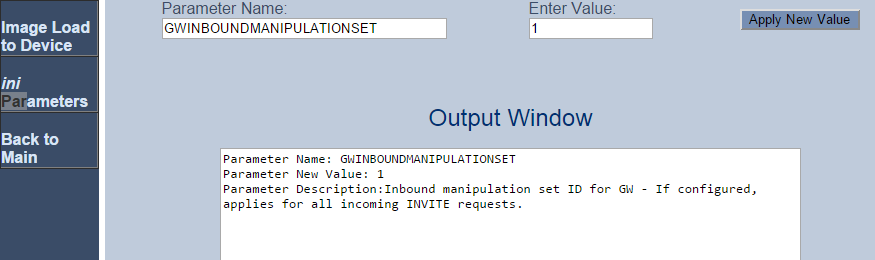
Open the INI parameters from the Admin Page (http://x.x.x.x/AdminPage), then enter GWINBOUNDMANIPULATIONSET with a value of 1 (or whichever Set ID you used for your Manipulation rule)
Once this was done, all reinvites back from Mediation with a=sendonly (call on hold) get translated to a=inactive and the gateway queues Kenny G or AC/DC. We can confirm the rule is applied and the RTP mode gets changed.
BOOM!!!
October 2014 update for Lync for Mac 2011 14.0.10
Grab it here: http://www.microsoft.com/en-us/download/details.aspx?id=36517
Biggest changes are Call/Conversation History, Media Resiliency (automatic reconnection) and OS X Yosemite support.
- Update enables users to view call history in Lync for Mac 2011
- Update for Lync for Mac 2011 enables users to store conversation history on an Exchange server
- Location is not displayed in Lync for Mac 2011 when users join a wireless network
- Error “One or more selected contacts cannot receive your calls” when you forward calls in Lync for Mac 2011
- Delegation relationship is broken after a delegate signs in to Lync for Mac 2011
- Computer shutdown is not processed when Lync for Mac 2011 is running
- Update implements media resiliency mode in Lync for Mac 2011
- Dial pad disappears when a user who is not enabled for EV joins a video conference or a video call in Lync for Mac 2011
- Update enables users to interact with a contact from the call history in Lync for Mac 2011
AudioCodes hanging up UM call mid-voicemail
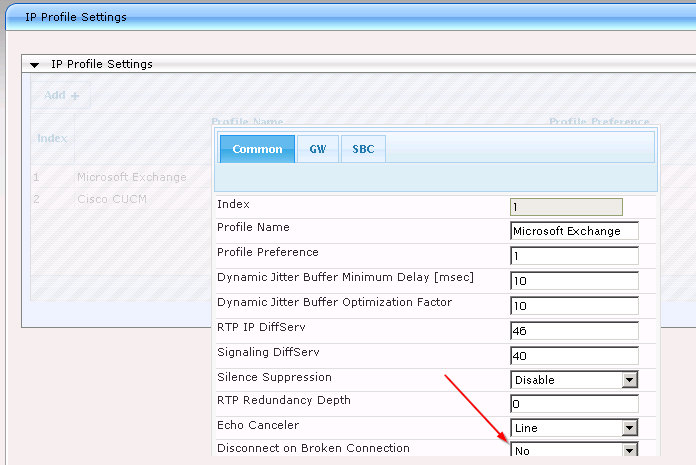
When integrating an AudioCodes gateway with Microsoft Exchange Unified Messaging, you may see an issue where the call is terminated while someone is leaving a voicemail longer than 30 seconds. This is because the gateway assumes the connection is broken the moment you start speaking, since UM is no longer sending RTP packets or silence suppression codes.
The solution is to turn of the Disconnect on Broken Connection on the IP profile used for your UM server within the AudioCodes gateway.
August 2014 Lync Phone Edition Updates
Microsoft released updates to Lync Phone Edition devices yesterday, including updates for devices like the popular Polycom CX600 and CX3000 that we use around the office.
An item worth mentioning is an update that enables non-EV or non-UC users to sign-in to Lync Phone Edition devices, and still use them for PC-to-PC calls, detailed here.
Here’s the download (for CX series devices): http://support.microsoft.com/kb/2988181. If you have other devices like Aastra or HP, there are other downloads out there.
LDWin: LLDP “Reader” for Windows
Useful little utility if you’re probing network ports to find out where you’re plugged in. This reads Link Layer Discovery Protocol (LLDP) or Cisco Discovery Protocol (CDP) packets coming in the interface you pick, and displays it all. Sure beats filtering Wireshark packets!
http://chall32.blogspot.com/2013/03/ldwin-link-discovery-for-windows.html
Default Zeacom Administrator credentials
New Lync Phone Edition July 2014 update
New July 2014 Lync Phone Edition updates: http://support.microsoft.com/kb/2973941
This cumulative update resolves the following issue:
2973943 Update for Lync Phone Edition to accommodate daylight saving time (DST) in Egypt and Morocco
Sophos UTM as Reverse Proxy for Lync 2013
Update: Sophos released an official guide on how to get Lync Web Services to work over the UTM’s WAF. https://sophserv.sophos.com/repo_kb/120454/file/Configuring%20UTM%20firewall%20for%20Lync%20connectivity.pdf
Using a Sophos UTM or Astaro Security Gateway (ASG) appliance? You can use it to reverse proxy to your Lync front ends!
v8 a feature called Web Application Firewall, which is a nicely wrapped version of Apache mod_proxy, and can be configured to reverse proxy your Lync Mobility and simple URLs, Office Web Apps and can also work with Exchange and pass Outlook Anywhere. The added benefit is that you can configure rules to block Cross-Site Scripting (XSS) and SQL Injection type attacks, among other things.
If you have the subscription, here’s how you set it up with Lync 2013:
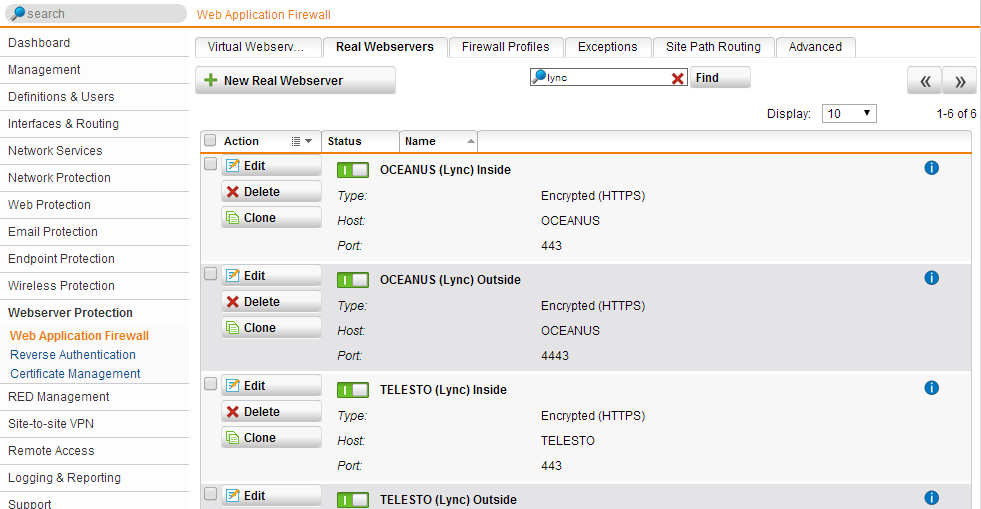
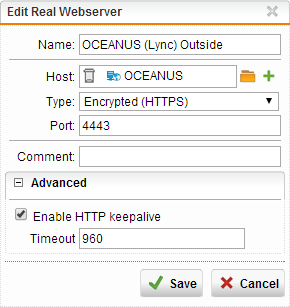
Configure your Lync Front Ends as Real Webservers. You will need to configure two servers for each FE, one for 8080 and another for 4443. If you plan on using the proxy for internal loopback (to avoid cert conflicts), then you will need 4 real servers, one for each port (80, 443, 4443, 8080). If you only want SSL, then skip the 80 and 8080:
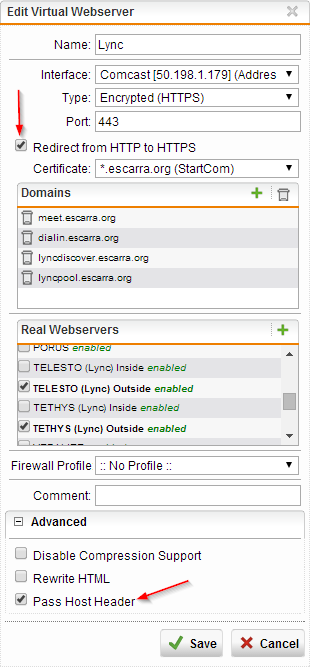
Then configure your Virtual Web Server (I will assume you already uploaded a valid certificate to the Sophos appliance). Make sure to check Pass Host Header, and you can enable HTTP redirection so your end users are happy when they skip HTTPS prefixes.
Save it, enable it, and DONE!
NOTE: If you have issues with the Lync iOS client resetting the connection, you can increase the timeout on the Real Webservers to 960 or 1200, but you will need to be on firmware version 9.204-19 or greater, since the feature was introduced then.
Certificates Unchained
Both Lync and Exchange rely heavily on public-key encryption using X.509 certificates (commonly known as SSL Certificates), and so they are required in every implementation. Regardless of whether you are using a public certification authority like DigiCert, or host your own internal CA, generating, installing and managing certificates can get pretty complex, especially when you have to deal with Intermediate Certificates.
Certificate Chains can be a confusing concept and hopefully I do a good job in trying to explain them with a real-world analogy. Here goes:
Let’s say you are John Doe, a fellow citizen that obeys the laws and respects the rules and guidelines put forth by society, and you’ve been asked to make a State of the Union speech on national television. Sounds crazy, I know, but I had a hard time coming up with a better situation… (comments?)
Here’s one issue to tackle as soon as you show up on that big screen: “Who’s THIS guy?”. You begin your speech, and in the first few statements you say that you’ve been granted authority to speak by Senator Joe Smith, and that any questions of authority should be directed to him. Officially, the Senator endorsed (or signed for) you, John Doe the citizen.
Now, most people may not know Senator Joe Smith, but they do know the President of the United States. If you were to call the Senator and ask him for his authority or credentials, he will say he has been granted permission to act on the President’s behalf for the purpose of assigning someone to speak at the State of the Union speech. In other words, the President endorsed (or signed for) the Senator, who in turn signed for you.
If we were to break this down, John Doe citizen is the holder of the end LEAF certificate, the Senator is the INTERMEDIATE authority, and the President is the ROOT Certification Authority… Makes sense so far?
You were never technically granted authority to speak directly by the President. In fact, you were never in contact with him, and were only granted authority by an intermediary that has been endorsed by him. In this case, the CHAIN is:
Root (President) >Intermediary (Senator) > You (Citizen).
If during the initial stages of your speech you were to have said the President gave you authority, and everyone went to check with him, they would find that statement to be false. The President never directly endorsed YOU, therefore the chain is broken and cannot be validated. There’s something missing, and that’s the information about the intermediary. If you never send that chain information, some (or most) will not trust you, even if you claim to be authentic.
What does that mean in IT terms? Make sure your certificate chain is followed, and organize your certificates properly in your Certificates MMC on each system that presents them. Follow these rules:
- Root CA certificates will always be self-signed and must be placed on the Trusted Root Certification Authorities store.
- Intermediate CA certificates will be signed by a Root CA or another Intermediate CA, and must be placed on the Intermediate Certification Authorities store.
- Your own certificates will be signed by either a Root CA (less likely) or an Intermediate CA (more likely), and should be stored in the Personal store.
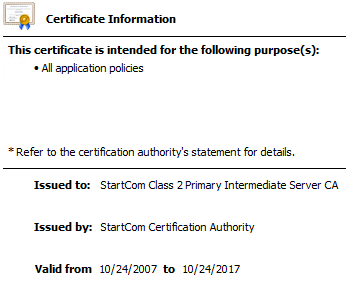
Here are samples screenshots of the public certs I am using for my Lync lab:
Root CA (notice how it’s self-signed):
Intermediate CA (signed by the above Root CA):
Chain:
Hope this article didn’t get too messy or confusing. If you have any questions, please drop me a comment!